Json Injection Cheat Sheet
Json Injection Cheat Sheet - Web use a safe, standard data interchange format such as json (via json_decode () and json_encode ()) if you need to pass. Injection attacks are where attackers run. Web in this article, we’ll take a look at how to use json. Web learn what is a json injection attack, how it works, and how to prevent it in web applications.
Web in this article, we’ll take a look at how to use json. Web learn what is a json injection attack, how it works, and how to prevent it in web applications. Web use a safe, standard data interchange format such as json (via json_decode () and json_encode ()) if you need to pass. Injection attacks are where attackers run.
Web learn what is a json injection attack, how it works, and how to prevent it in web applications. Injection attacks are where attackers run. Web use a safe, standard data interchange format such as json (via json_decode () and json_encode ()) if you need to pass. Web in this article, we’ll take a look at how to use json.
What Is JSON? Syntax, Examples + Cheat Sheet
Web in this article, we’ll take a look at how to use json. Injection attacks are where attackers run. Web learn what is a json injection attack, how it works, and how to prevent it in web applications. Web use a safe, standard data interchange format such as json (via json_decode () and json_encode ()) if you need to pass.
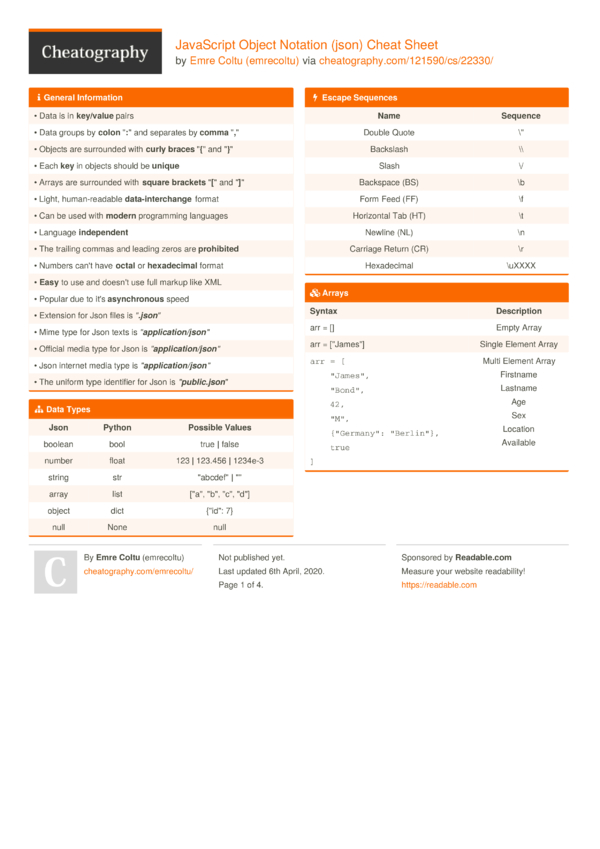
JavaScript Object Notation (json) Cheat Sheet by emrecoltu Download
Web learn what is a json injection attack, how it works, and how to prevent it in web applications. Web in this article, we’ll take a look at how to use json. Web use a safe, standard data interchange format such as json (via json_decode () and json_encode ()) if you need to pass. Injection attacks are where attackers run.
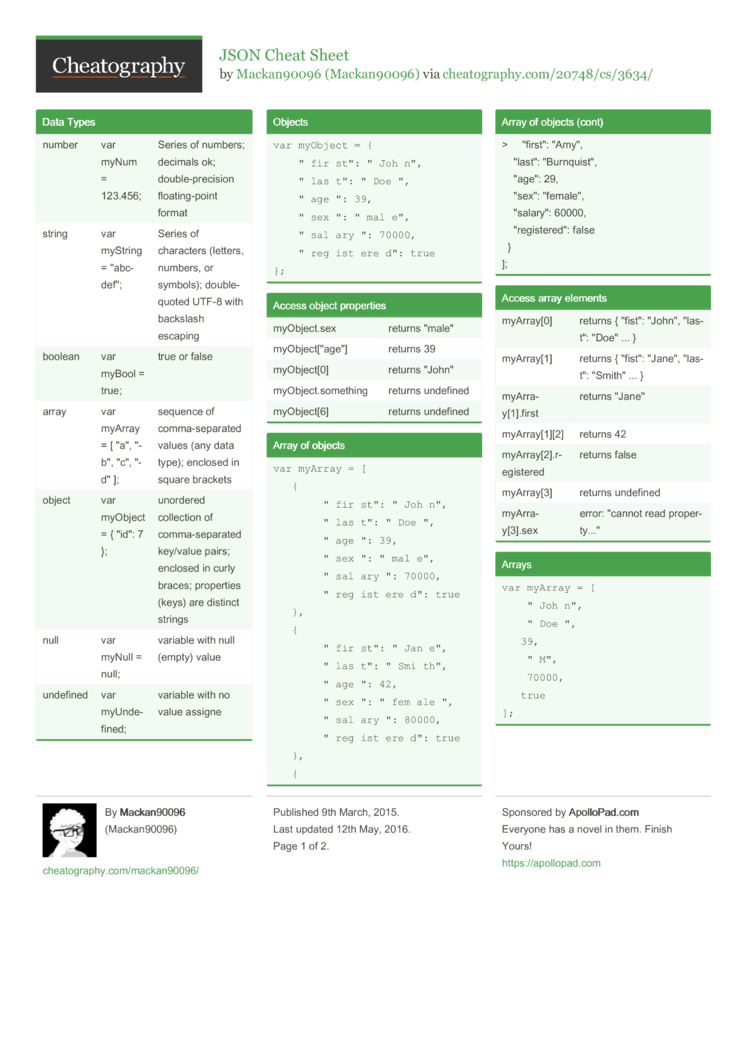
Json Cheat Sheet
Web in this article, we’ll take a look at how to use json. Injection attacks are where attackers run. Web use a safe, standard data interchange format such as json (via json_decode () and json_encode ()) if you need to pass. Web learn what is a json injection attack, how it works, and how to prevent it in web applications.
Json Sql Injection Cheat Sheet herenfil
Injection attacks are where attackers run. Web in this article, we’ll take a look at how to use json. Web learn what is a json injection attack, how it works, and how to prevent it in web applications. Web use a safe, standard data interchange format such as json (via json_decode () and json_encode ()) if you need to pass.
Mysql Syntax Cheat Sheet
Web use a safe, standard data interchange format such as json (via json_decode () and json_encode ()) if you need to pass. Web in this article, we’ll take a look at how to use json. Injection attacks are where attackers run. Web learn what is a json injection attack, how it works, and how to prevent it in web applications.
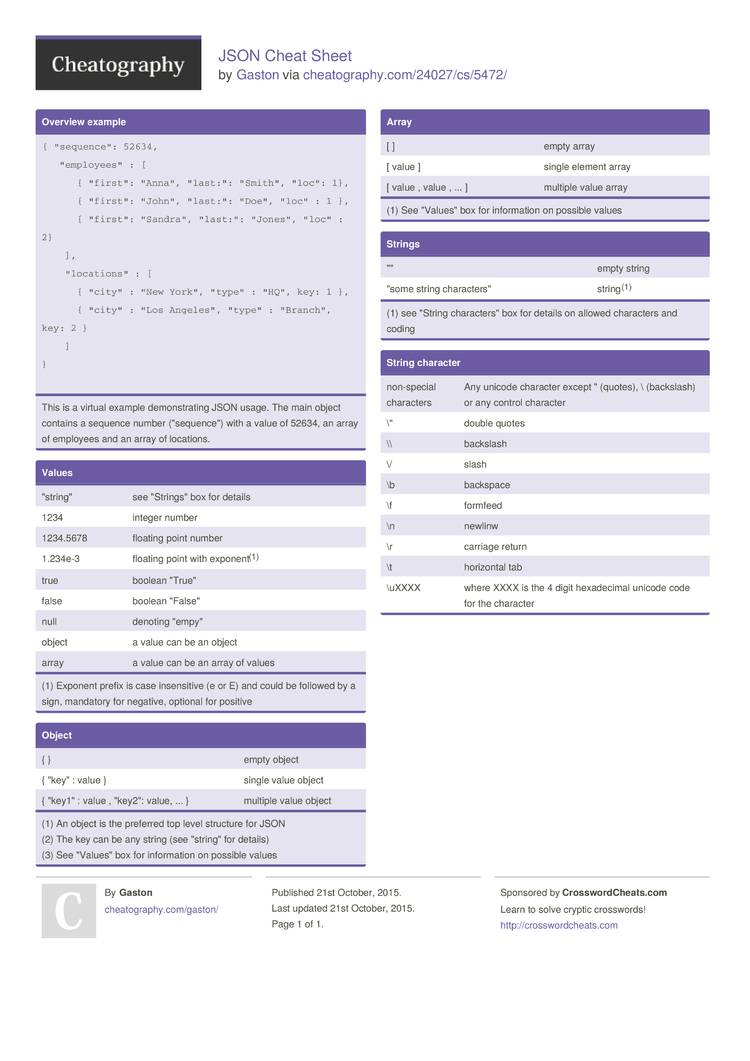
JSON Cheat Sheet by Gaston Download free from Cheatography
Web learn what is a json injection attack, how it works, and how to prevent it in web applications. Web in this article, we’ll take a look at how to use json. Web use a safe, standard data interchange format such as json (via json_decode () and json_encode ()) if you need to pass. Injection attacks are where attackers run.
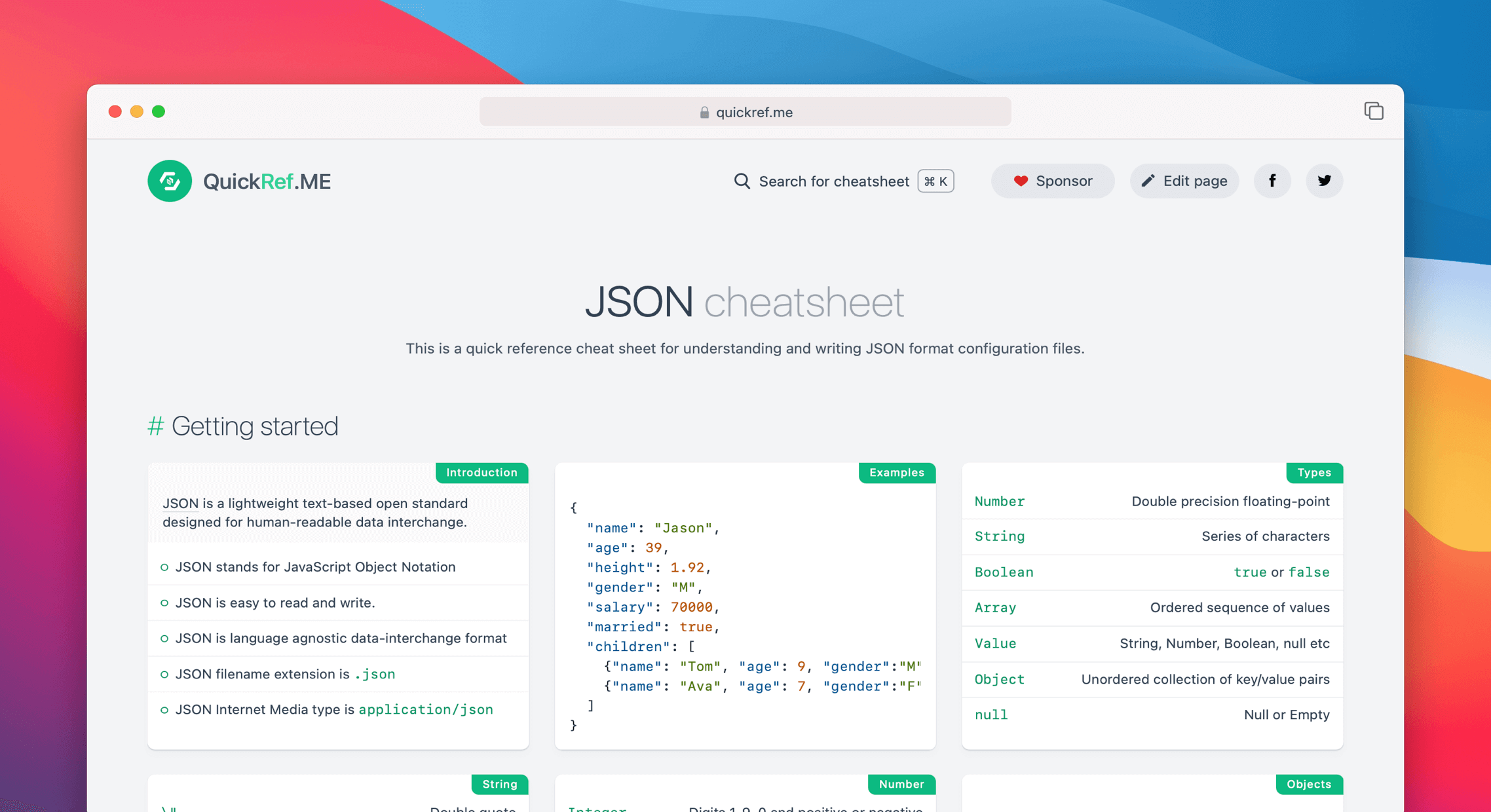
JSON Cheat Sheet & Quick Reference
Web use a safe, standard data interchange format such as json (via json_decode () and json_encode ()) if you need to pass. Injection attacks are where attackers run. Web learn what is a json injection attack, how it works, and how to prevent it in web applications. Web in this article, we’ll take a look at how to use json.
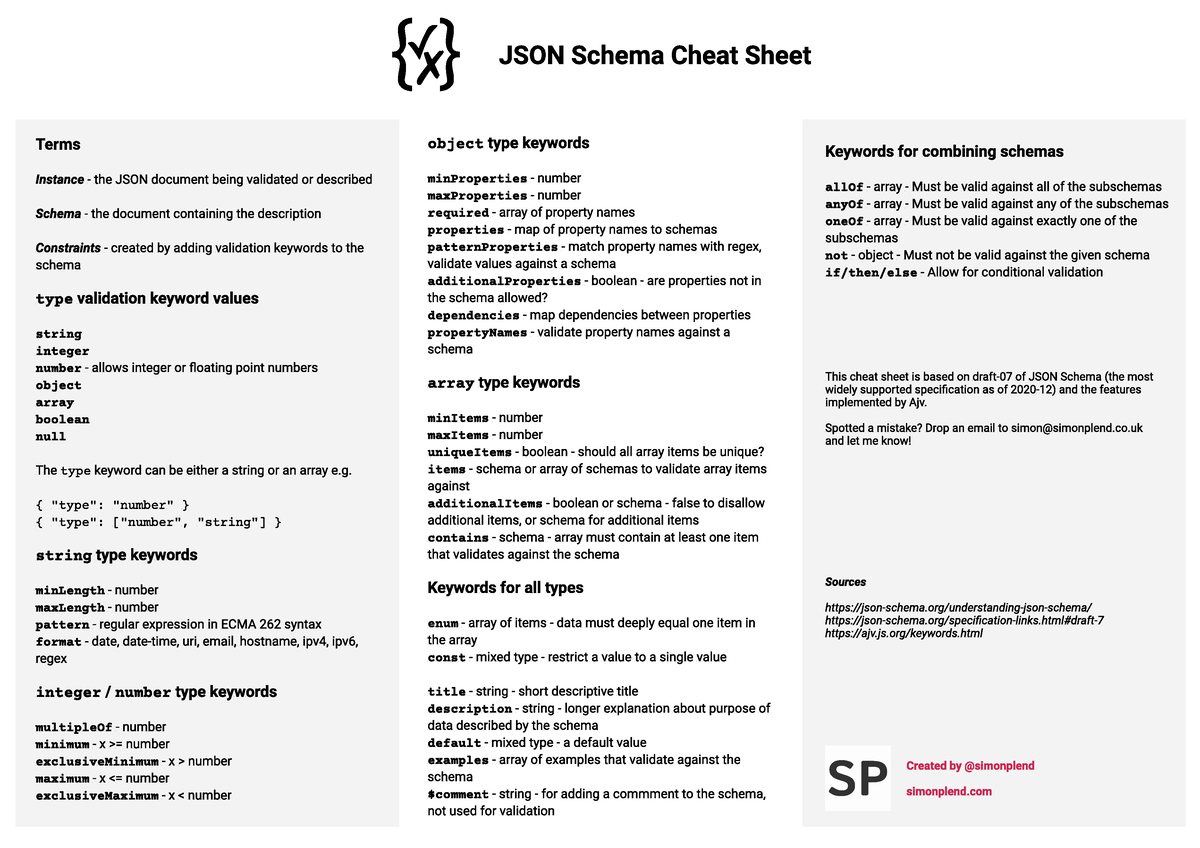
JSON Schema Cheat Sheet v1 Studocu
Web learn what is a json injection attack, how it works, and how to prevent it in web applications. Web use a safe, standard data interchange format such as json (via json_decode () and json_encode ()) if you need to pass. Web in this article, we’ll take a look at how to use json. Injection attacks are where attackers run.
JSON Injection · Issue 14 · google/jsontoken · GitHub
Injection attacks are where attackers run. Web learn what is a json injection attack, how it works, and how to prevent it in web applications. Web use a safe, standard data interchange format such as json (via json_decode () and json_encode ()) if you need to pass. Web in this article, we’ll take a look at how to use json.
Json / YAML & JsonSchema cheat sheet Un peu de dev et de géomatique
Web in this article, we’ll take a look at how to use json. Web use a safe, standard data interchange format such as json (via json_decode () and json_encode ()) if you need to pass. Injection attacks are where attackers run. Web learn what is a json injection attack, how it works, and how to prevent it in web applications.
Web Learn What Is A Json Injection Attack, How It Works, And How To Prevent It In Web Applications.
Injection attacks are where attackers run. Web use a safe, standard data interchange format such as json (via json_decode () and json_encode ()) if you need to pass. Web in this article, we’ll take a look at how to use json.